Security Advisory affecting DSCS9X and DSCS95
Summary
A security issue has been identified with the firmware on DSDevices DSCS95 and DSCS9X devices, which may allow an attacker on the same local network as the device to execute arbitrary commands on the device as the system user. The issue is outlined in DSDevices' security advisory.
New firmware has been released to rectify the problem, and we strongly recommend all owners of DSCS9X or DSCS95 devices to check if their units are affected, and either upgrade to the latest firmware version, or apply the settings change detailed below.
Firmware versions are named by their build date. For example, firmware version 20230109 refers to 9th January 2023.
For the DSCS9X, firmware version 20240909 and later resolves the issue.
For the DSCS95, firmware version 20240904 and later resolves the issue.
To see your current firmware version, from the Launcher click the Settings icon, Device Preferences, About and scroll down to the bottom where you’ll find the Build section. The firmware version is listed near to the end of the line:
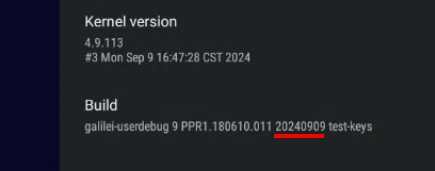
In the screenshot from a DSCS9X, version 20240909 is shown which is not vulnerable to this issue.
If your firmware version is lower than 20240909 in the case of a DSCS9X, or lower than 20240904 in the case of a DSCS95, then the device is vulnerable and you should take action to secure the device.
Our support team can assist you in determining whether or not your devices are vulnerable. If you require assisance, please see the "How to get help" section below.
Mitigation
Updated firmware is available to resolve this issue for both devices.
If your local network configuration makes it impossible for untrusted users to make connections to your devices across the network, then any one of the following mitigations will resolve the issue:
- Upgrading to Xibo for Android v4 R405 or Xibo for Android v3 R313 or later versions
- Firmware upgrade via OTA
- Running a command from the CMS
- Making the configuration change detailed below
If the local network your device is connected to is open to untrusted users (e.g. guest/open wifi networks without Client device isolation enabled, shared wired or wifi networks), then we’d recommend doing a factory reset before applying the OTA upgrade, or performing a full firmware reflash to ensure that the device is returned to a healthy condition.
Please find mitigation steps for each scenario below.
Upgrade Xibo for Android
Whilst the vulnerability is not related to Xibo for Android, installing v4 R405 or v3 R313 or later versions will automatically mitigate the vulnerability each time the Player starts up. You can upgrade Xibo for Android versions directly from the CMS without needing to visit each DSDevice. We'd recommend upgrading a test device first before applying the upgrade to multiple devices.
Firmware Upgrade via OTA
Details of how to upgrade via OTA are available here:
DSCS9X OTA Upgrade Instructions
DSCS95 OTA Upgrade Instructions
Run a command from the CMS
A command can be scheduled to run periodically on your devices from the CMS to mitigate the vulnerability.
Start by defining a new Command in your CMS.
Name: Turn Off USB Debugging
Reference: xUSBDB
Command - Free Text: settings put global adb_enabled 0
Validation: Leave this empty
Available On: Android
Save your command.
Now from the Schedule page of the CMS, schedule that command to run on your DSCS95 and/or DSCS9X devices. We'd recommend having that command daily for 1-2 weeks. Ensure that all DSCS9X/95 devices have connected to the CMS and were powered on and running Xibo for Android at the time your commands were scheduled to run.
Ideally you should upgrade to Xibo for Android v4 R405 or v3 R313 and then remove the command from your schedule, and from Commands.
Configuration Change
If you are not able, or do not wish to upgrade the firmware on your device, you can instead make a configuration change on the device to mitigate the vulnerability - however note that this configuration change will not persist across a factory reset, so you will need to ensure that you reapply the change if you factory reset the device in future.
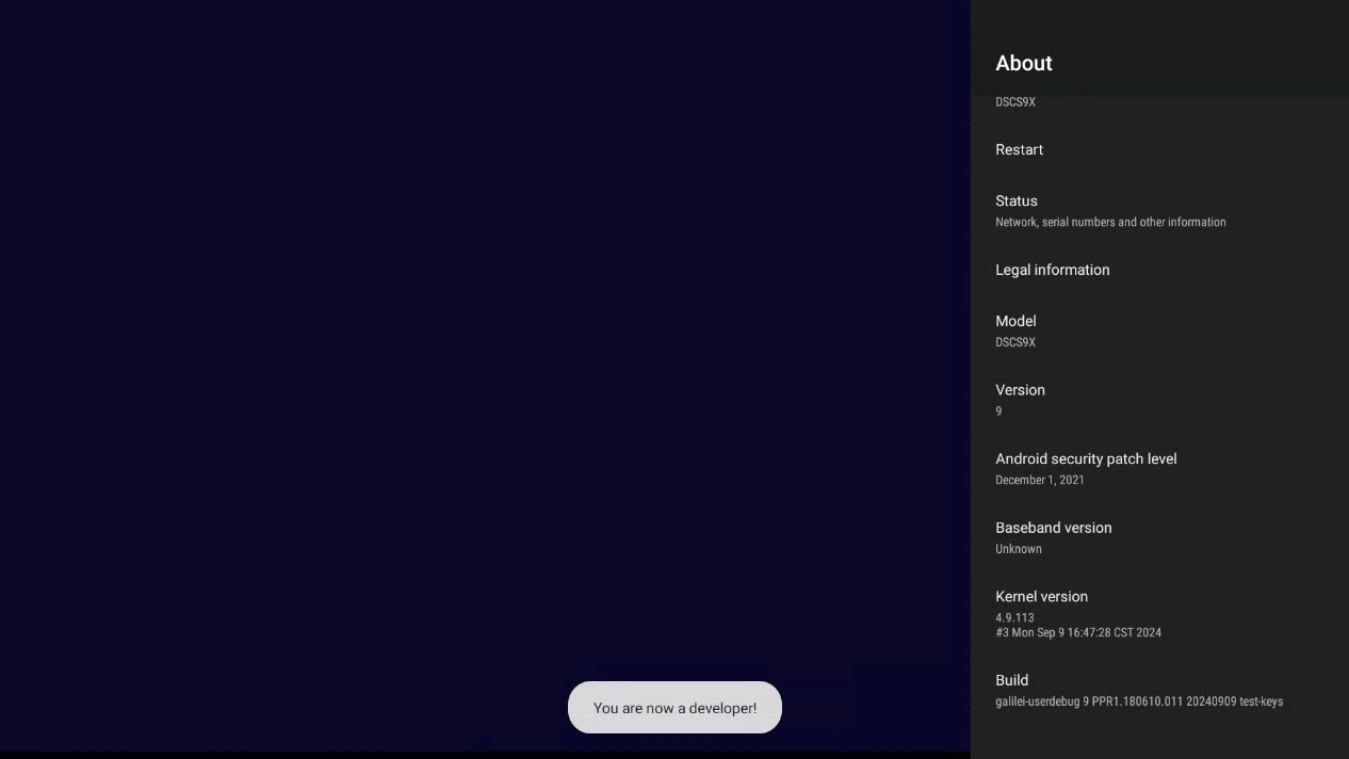
From the Launcher, click on Settings, Device Preferences, About. Scroll down to show the Build section, and click on the word Build seven times in a row, or until the toast “You are now a developer!” appears:
Now go back to the Launcher, and click Settings, Device Preferences, Developer Options. Scroll down to the Debugging section, and ensure USB debugging is turned off.
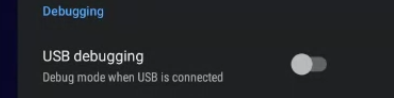
Optionally turn off “Enable developer options” at the top of the list to re-hide the Developer Options menu.
Factory Reset and OTA
Backup any apps, settings or configuration you may need to restore on to your device, as a factory reset will wipe all data from it.
To perform a factory reset, from the Launcher, click on Settings, Device Preferences, Reset. Click Reset again. The device will reboot.
Immediately apply the OTA upgrade as detailed above before connecting your device to the local network. You can then restore any data and reconfigure any apps as required.
Full Reflash
Backup any apps, settings or configuration you may need to restore on to your device, as a factory reset will wipe all data from it.
DSCS9X Firmware Reflashing Instructions
DSCS95 Firmware Reflashing Instructions
How to get help
If you need help to understand if your device is vulnerable to this issue, or assistance in applying one of the mitigation options described above, please contact the Helpdesk. You can do this from My Account - Tickets.
Disclosure Timeline
28th August 2024 - Xibo Signage was notified of a vulnerability in the firmware of DSCS9X device.
29th August 2024 - Xibo Signage investigated the issue internally and confirmed the problem applied to both DSCS9X and DSCS95 devices, across all released firmware versions.
29th August 2024 - Xibo Signage disclosed the vulnerability to DSDevices.
6th September 2024 - Fixed DSCS95 firmware made available via the Xibo Signage website, and on all devices shipping from the DSDevices warehouse in the UK.
11th September 2024 - Fixed DSCS9X firmware made available via the Xibo Signage website, and on all devices shipping from the DSDevices warehouse in the UK.
19th September 2024 - Public disclosure

.png)
